Once you start adopting a cloud service such as Microsoft Azure, one of the first tasks should be looking at how to enforce organisational and best-practice policies at scale when resources are being created.
Fortunately Microsoft makes enforcing policies relatively straightforward via a service called Azure Policy. It combines a number of best practice, out-of-the-box policies with the ability for you to also create your own custom policy definitions. You can setup guardrails and enforce compliance easily.
The best bit? Aside from Azure Arc resources, Azure Policy is available free of charge.
Setting up policies
Once you have an active Azure subscription, the first thing you’ll want to do is sign in to the Azure portal and open the ‘Policy’ service. You can find this by searching for ‘Policy’.
If you haven’t setup any policies and you have no provisioned resources, you should see a dashboard showing a 100% compliance rate. Otherwise the dashboard may show you issues that require attention with your provisioned resources.
The ‘Getting Started’ tab allows you to quickly setup policy assignments for your cloud environment. This includes things such as blocking the provision of various resource types or requiring tags on resources.
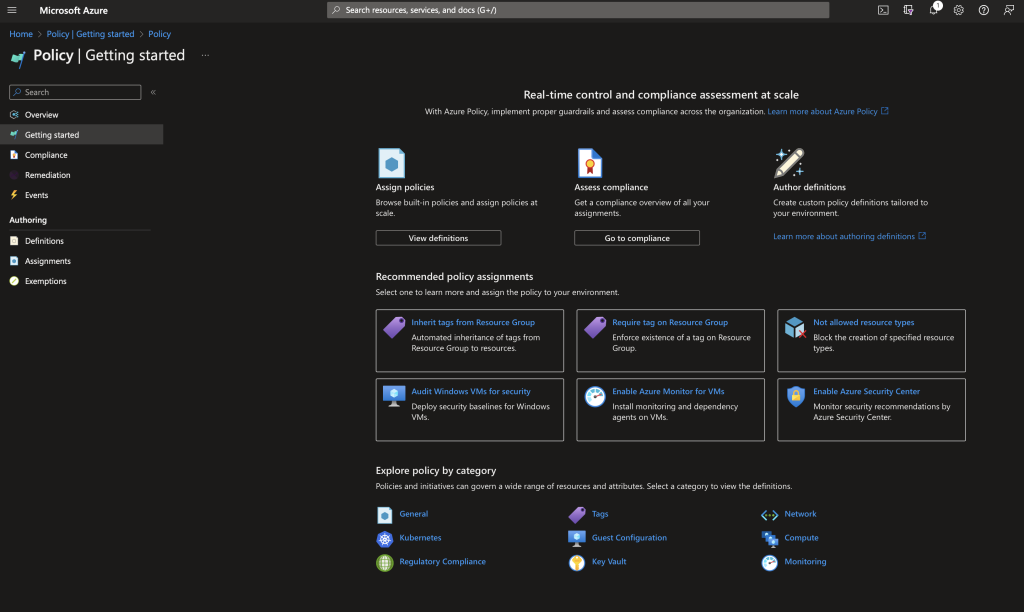
The ‘Getting Started’ tab for Azure Policy
Alternatively you can select “Definitions” under “Authoring” and browse the complete list of policy definitions that can be applied.
Before configuring a policy, consider whether you want to retrospectively apply a policy to existing Azure resources or whether it should only apply to new resources being provisioned.
By default policies only apply to new resources, but you can update existing resources after the policy has been assigned.
Once you select a policy, you can configure the following:
Scope: The tenant, management group, subscription (optional) and resource group (optional) that the policy will apply to
Basics: The policy definition, assignment name and brief description of the policy. You can also specify whether the policy is enforced or disabled, and see who assigned the policy
Parameters: Some policies may require additional parameters. For example, the ‘Not allowed resource types’ policy requires you to select the types of resources you want to prohibit from being provisioned
Remediation: If you’re deploying a policy with the
deployIfNotExistsand modify effect types you’ll need to provide a managed identity that can be used to edit tags and deploy resources where required. You may also need to configure role permissionsNon-compliance message: Message to show when a resource or modification is denied due to the policy, or if a resource is presently non-compliant
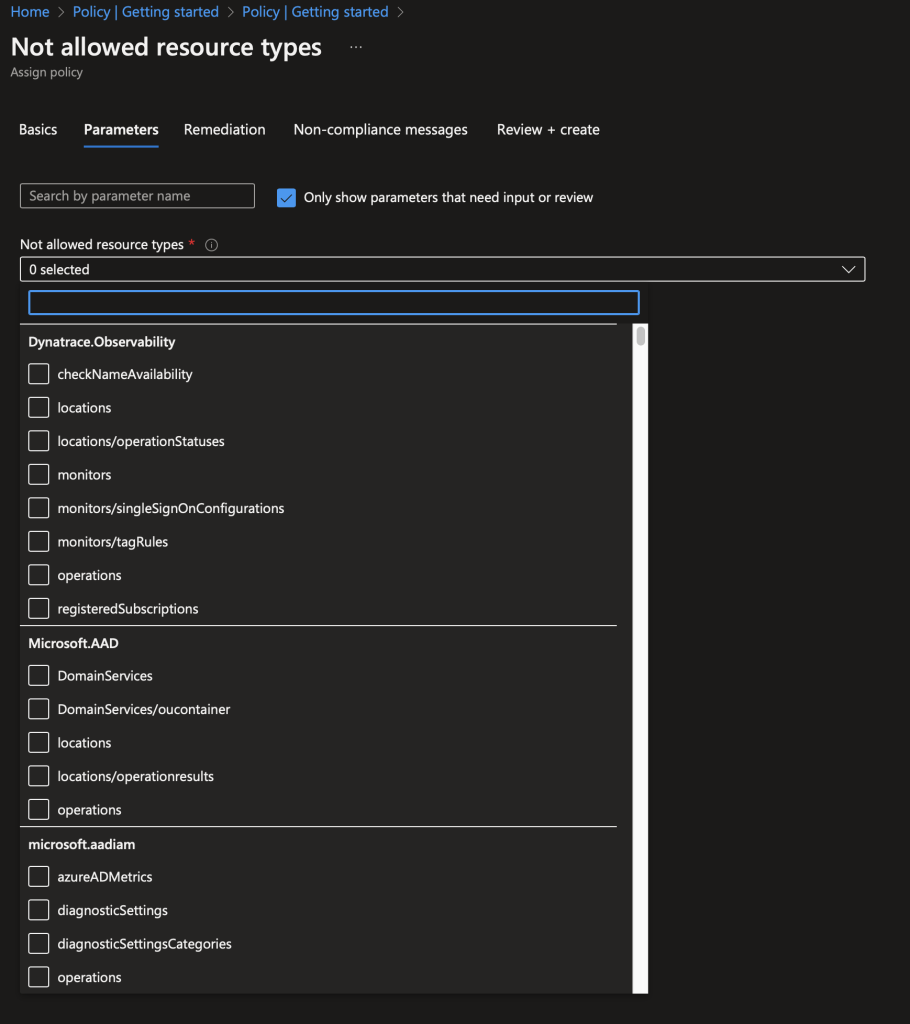
Where needed, provide Azure policy parameters
Monitoring compliance
Once you’ve configured your policies, the “Compliance” tab will update to show resources and their compliance state.
The list of resources shown can be filtered by scope (management group, subscription, resource group or resource type), definition type (all, initiative or policy), compliance state (such as compliant, non-compliant, not registered) and by name or ID.