Category: Azure
-

Microsoft Azure AD to become Microsoft Entra ID
Microsoft has this week revealed that by the end of 2023, Azure AD will be known as Entra ID, joining the other identity products already in the Entra suite. In a post on the Microsoft blog, Joy Chik, President, Identity & Network Access said that Entra ID will join Entra Permissions Management, Entra Verified ID,…
-
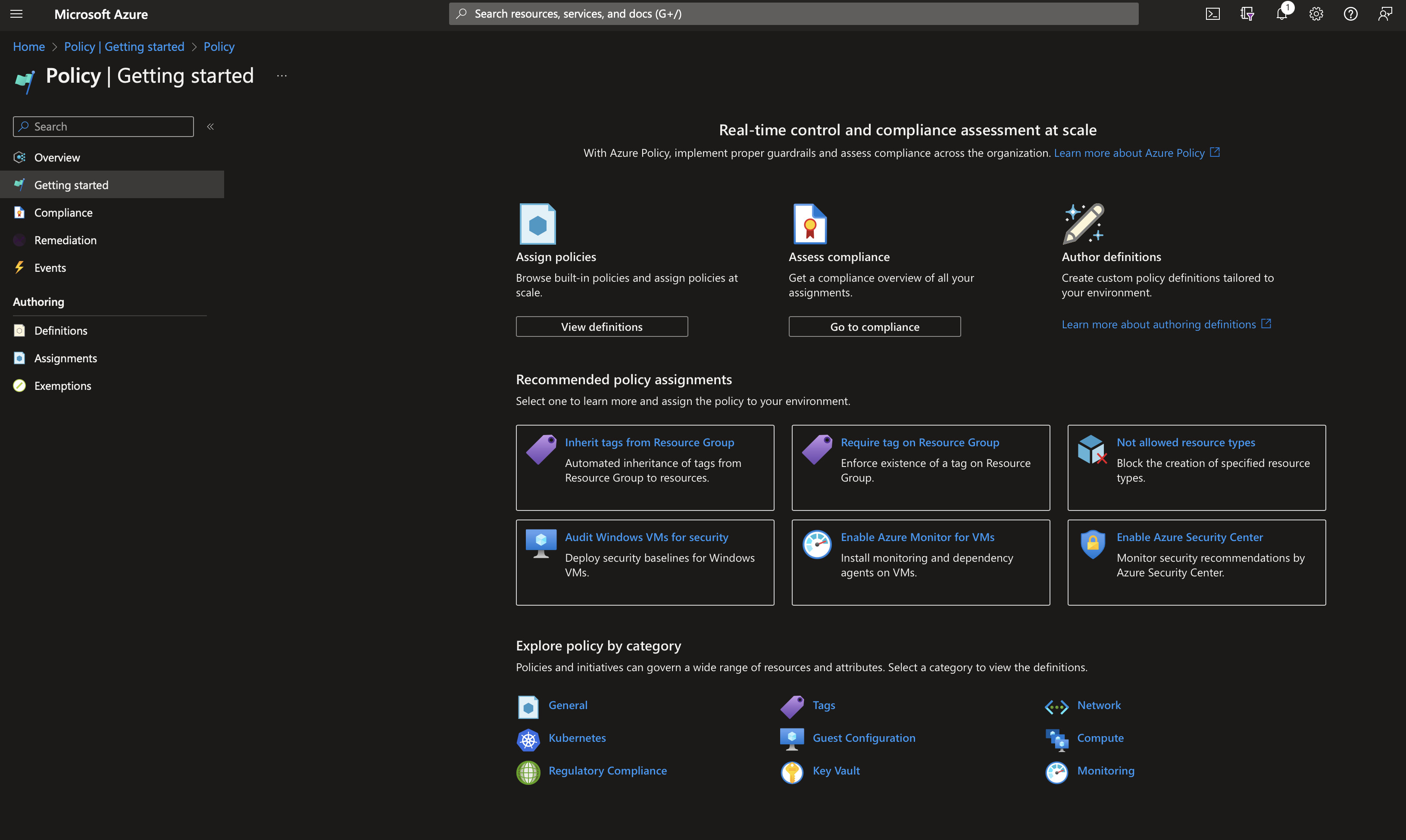
Getting started with Azure Policies
Once you start adopting a cloud service such as Microsoft Azure, one of the first tasks should be looking at how to enforce organisational and best-practice policies at scale when resources are being created.
-

Guide to Azure DevOps certification
Are you looking to become certified in Azure DevOps? If so, read on to find out more about what official Microsoft certifications are available. The pathway to Azure DevOps certification The first certification you’ll want to get is for Azure Fundamentals (AZ-900). This covers the basics about Azure, including generic cloud concepts as well as…
-
How to query multiple Azure Application Insights instances at once
Do you have multiple Azure Application Insights instances that you’d like to query at once? Perhaps you’re trying to see all errors across multiple environments, each with their own App Insights instance? When using the Azure Portal, querying multiple instances is straightforward. How to query across multiple App Insight instances First, login to the Azure…
-

Getting started with Azure Bicep
Bicep is a new language from Microsoft that allows you to easily specify your Azure infrastructure as code. It’s an improvement on writing Azure Resource Manager (ARM) templates directly by better supporting features such as type safety and code modularity and reuse. That said, Bicep still has a very close relationship with ARM templates. In…
-
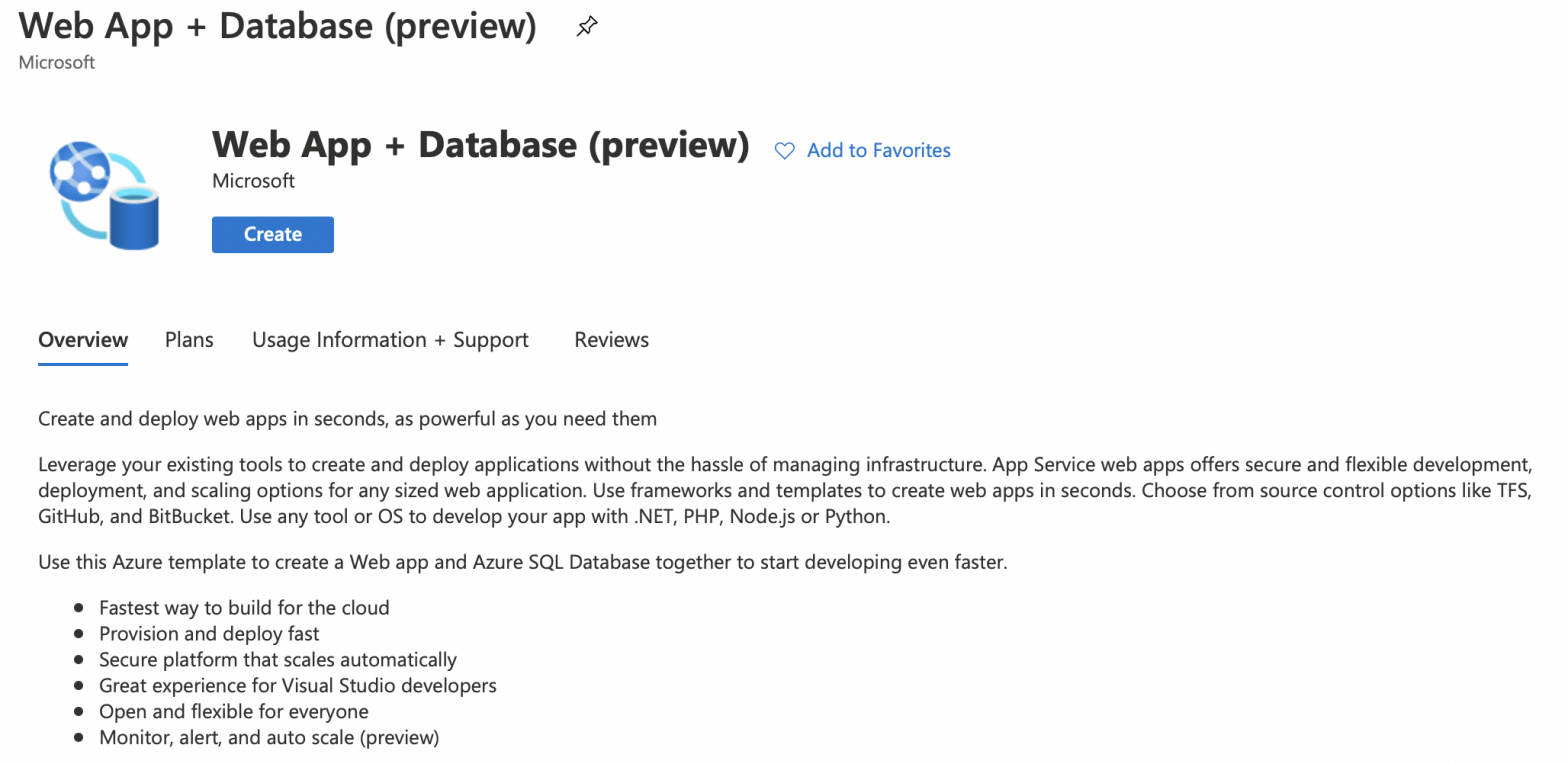
How to create an Azure app service with a database
Need to deploy your app to an Azure app service, and rely on a database such as Postgres or Azure SQL? Microsoft is now previewing a new blade in the Azure portal that lets you quickly spin up an Azure app service with an associated database. Supported database engines for the preview are Postgres or…